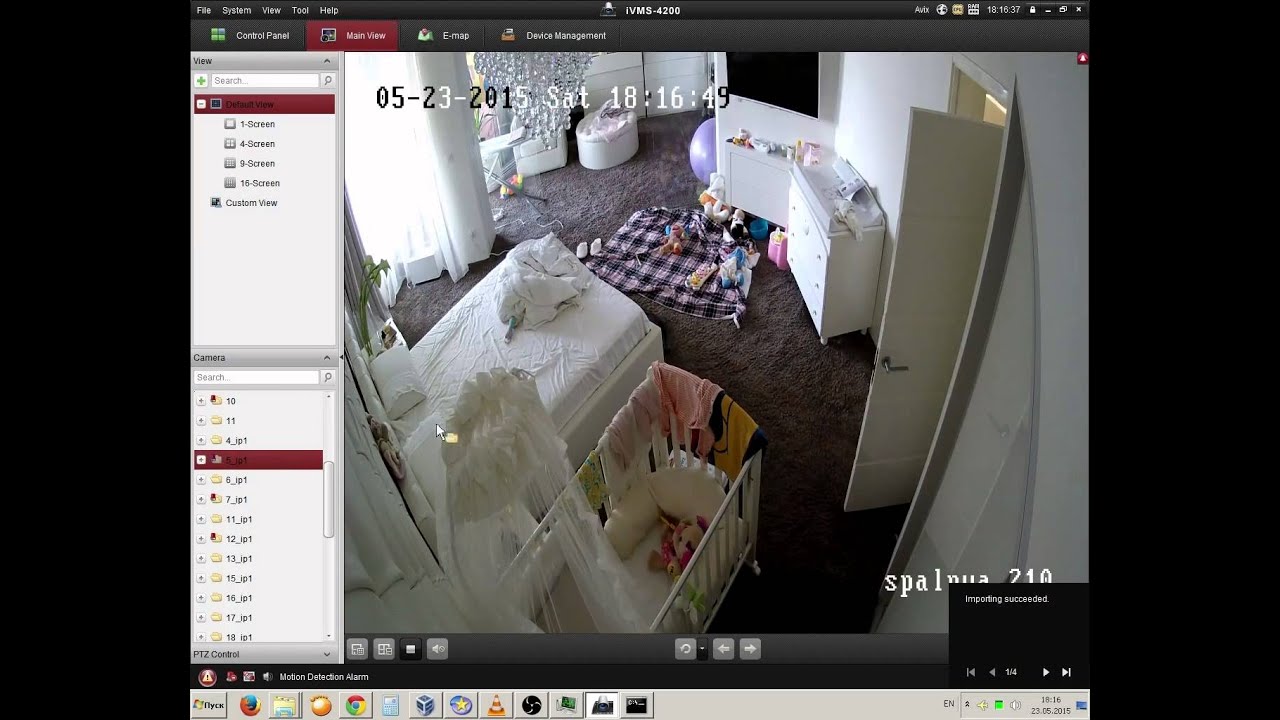
Imagine this: You’re scrolling through Telegram when you stumble upon a mysterious channel sharing live feeds from what seems to be private security cameras. Creepy, right? But here's the kicker—these aren’t just random feeds; they’re hacked IP cameras, giving strangers a front-row seat to people's private lives. This is no longer just a plot twist in a thriller movie—it's happening in real life. Hacked IP cam Telegram channels have become a growing concern, exposing vulnerabilities in our digital world.
The phrase "hacked IP cam Telegram" might sound like something out of a sci-fi novel, but it's a very real issue that’s affecting countless individuals worldwide. With the rise of internet-connected devices, the risk of unauthorized access has skyrocketed. From baby monitors to office security systems, no one is truly safe from prying eyes. So, how does this happen, and what can we do to protect ourselves? Let’s dive deeper.
In this article, we’ll explore the dark side of hacked IP cameras and the role Telegram plays in facilitating these breaches. We’ll also discuss the potential consequences, legal implications, and most importantly, how you can safeguard your devices. Whether you're tech-savvy or just trying to stay safe online, this guide will equip you with the knowledge you need to protect your privacy.
Read also:Travis County Expo Center Your Ultimate Guide To The Heart Of Texas Events
Here’s a quick overview of what we’ll cover:
- What are Hacked IP Cams?
- How Telegram Channels Exploit These Devices
- Why This Is a Growing Problem
- Steps to Protect Your IP Cameras
- Legal Ramifications of Hacking IP Cameras
What Exactly Are Hacked IP Cams?
Let’s break it down. An IP camera, short for Internet Protocol camera, is a type of digital video camera that sends and receives data over a network or the internet. They’re commonly used for home security, business surveillance, and even baby monitoring. But here’s the thing: if these devices aren’t properly secured, hackers can exploit them to gain unauthorized access. Once inside, they can stream live footage, record private moments, or even sell the feeds on platforms like Telegram.
It’s not just about privacy invasion—it’s about trust. Imagine discovering that your own home has been broadcasting live feeds to strangers without your knowledge. Scary, right? That’s why understanding the mechanics of how IP cameras get hacked is crucial. It’s not always about advanced hacking skills; sometimes, it’s as simple as leaving default passwords unchanged or failing to update firmware.
How Do IP Cameras Get Hacked?
Hacked IP cams often fall victim to simple oversights. Here are some common methods hackers use:
- Default Passwords: Many users never change the default login credentials that come with their devices. Hackers have databases of these default passwords and can easily gain access.
- Unpatched Vulnerabilities: Manufacturers sometimes release updates to fix security flaws, but users don’t always install them. This leaves devices exposed to known exploits.
- Weak Network Security: If your home Wi-Fi network isn’t secure, hackers can infiltrate it and gain access to connected devices.
- Misconfigured Settings: Some IP cameras come with settings that allow remote access. If not properly configured, this can be an open invitation for hackers.
These vulnerabilities make it easier for malicious actors to infiltrate devices and share the feeds on platforms like Telegram.
Telegram Channels: The New Playground for Hackers
Telegram, a popular messaging app known for its end-to-end encryption, has become a hotspot for hackers sharing hacked IP cam feeds. While the platform itself isn’t inherently bad, its anonymity feature makes it an attractive option for those looking to distribute illicit content. These channels often operate under the radar, making it difficult for authorities to shut them down.
Read also:Embarc Fresno Your Ultimate Guide To Unveiling The Hidden Gem
So, how do these channels work? Typically, hackers will join or create groups where they share links to live streams from compromised IP cameras. These feeds can range from private homes to public spaces, and the content is often disturbing. What’s worse is that many users who join these channels may not even realize the ethical and legal implications of what they’re viewing.
Why Does Telegram Allow This?
Telegram has a strict policy against illegal content, but enforcement can be tricky. With millions of users and channels, it’s nearly impossible to monitor every single one. Additionally, some hackers use encrypted channels, making it even harder for moderators to detect and remove harmful content. While Telegram has taken steps to combat this issue, the problem persists.
Why Is This a Growing Concern?
There are several reasons why hacked IP cam Telegram channels are becoming more prevalent:
- Increased Adoption of Smart Devices: More people are using IP cameras for personal and professional purposes, increasing the potential pool of targets.
- Advancements in Technology: As technology evolves, so do the tools available to hackers. What was once difficult to achieve is now easier than ever.
- Human Error: Users often neglect basic security practices, leaving their devices vulnerable to attacks.
Combine these factors with the anonymity provided by platforms like Telegram, and you’ve got a recipe for disaster. But don’t worry—we’ll cover how you can protect yourself in the next section.
Steps to Protect Your IP Cameras
Prevention is key when it comes to safeguarding your devices. Here are some actionable steps you can take:
Change Default Passwords
One of the easiest ways to protect your IP camera is by changing the default password. Use a strong, unique password that includes a mix of letters, numbers, and symbols. Avoid using common phrases or easily guessable information like birthdays or pet names.
Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification before granting access. Many IP cameras and associated apps offer this feature, so be sure to enable it if available.
Keep Firmware Updated
Manufacturers frequently release updates to address security vulnerabilities. Make it a habit to check for and install these updates regularly. This ensures your device has the latest protections against potential threats.
Use a Secure Network
Your home Wi-Fi network should be secured with a strong password and WPA3 encryption. Avoid using public Wi-Fi networks to access your IP camera, as these can be easily compromised.
Limit Remote Access
If you don’t need remote access to your IP camera, disable this feature. If you do need it, ensure it’s properly configured and only accessible through secure channels.
Legal Ramifications of Hacking IP Cameras
Hacking IP cameras isn’t just unethical—it’s illegal. In many countries, unauthorized access to someone else’s device is considered a criminal offense. Penalties can include hefty fines, imprisonment, or both. Even viewing hacked feeds without participating in the hacking itself can have legal consequences.
Here are some key points to consider:
- Privacy Laws: Most countries have strict privacy laws that protect individuals from unauthorized surveillance.
- Cybersecurity Regulations: Governments are increasingly implementing regulations to combat cybercrime, including IP camera hacking.
- International Cooperation: Law enforcement agencies worldwide are working together to track down and prosecute hackers involved in these activities.
It’s important to remember that ignorance of the law isn’t an excuse. If you stumble upon a hacked IP cam feed, resist the temptation to view it and report it to the appropriate authorities instead.
Real-Life Examples of Hacked IP Cams
To illustrate the severity of this issue, let’s look at a few real-life examples:
Case Study 1: The Baby Monitor Breach
In 2020, a family in Florida discovered that their baby monitor had been hacked. The intruder not only watched their child but also spoke to them through the device’s speaker. This incident highlighted the importance of securing all smart devices, no matter how small they may seem.
Case Study 2: The Office Surveillance Leak
A small business in Europe fell victim to a hacking attack that exposed their office surveillance system. The hackers streamed the footage on a Telegram channel, revealing sensitive company information. This breach cost the business thousands in damages and damaged their reputation.
Future Implications and Solutions
As technology continues to evolve, so too will the methods used by hackers. However, there are promising solutions on the horizon. For example, advancements in AI and machine learning are being used to detect and prevent unauthorized access to devices. Additionally, manufacturers are becoming more proactive in addressing security concerns, releasing regular updates and offering better customer support.
What Can You Do?
Stay informed about the latest threats and take proactive steps to protect your devices. Educate yourself and others about the importance of cybersecurity. By working together, we can create a safer digital environment for everyone.
Conclusion: Take Control of Your Privacy
Hacked IP cam Telegram channels are a stark reminder of the dangers lurking in our digital world. While the thought of someone watching you without your knowledge is unsettling, there are steps you can take to protect yourself. By understanding the risks and implementing security best practices, you can minimize the chances of falling victim to these attacks.
We encourage you to share this article with friends and family to raise awareness about the issue. Together, we can make the internet a safer place. And remember, if you ever come across a hacked IP cam feed, report it immediately to the authorities. Your actions could help prevent someone else from becoming a victim.
.png)